Twice the fun
Officially a weekly newsletter | Real estate mishap | Gov hit again | PERSONAL File sharing
Well, it’s official… I am now a proud owner of an email newsletter 🤗. Or as some have told me - A ‘Blog’ or ‘Rant’ 😆.
Well, you can call it whatever you like as long as it’s providing you value, you enjoy reading it and you feel it is worth sharing with those in your network.
When I wrote last week’s edition of KCS and shared it with the world I would have never thought that 36 people hand over their email to me (or Substack in this case) or even read the thing in the first place.
I appreciate it and thanks for sharing with those you know!
On that note, I just want to take a minute to assure you that I or Substack will never use your email to send you unsolicited emails, on-sell your data or anything along those lines. One of the main reasons I chose substack as my newsletter (i’m just going to call it this from now on) platform was because I will always own the content and more importantly, the relationship with you - my subscribers.
Alright, let’s talk cybersecurity. Because, you know, that’s why you’re really here. But before we get into it, I thought the following meme outlines what this newsletter is all about.
Today in 10 minutes or less, you’ll get:
A Chart of the week Outlining some numbers about the costs of cybercrime
My Weekly Thoughts on recent data breaches which I think you should know about and why
Advice and points to consider when sharing your personal data
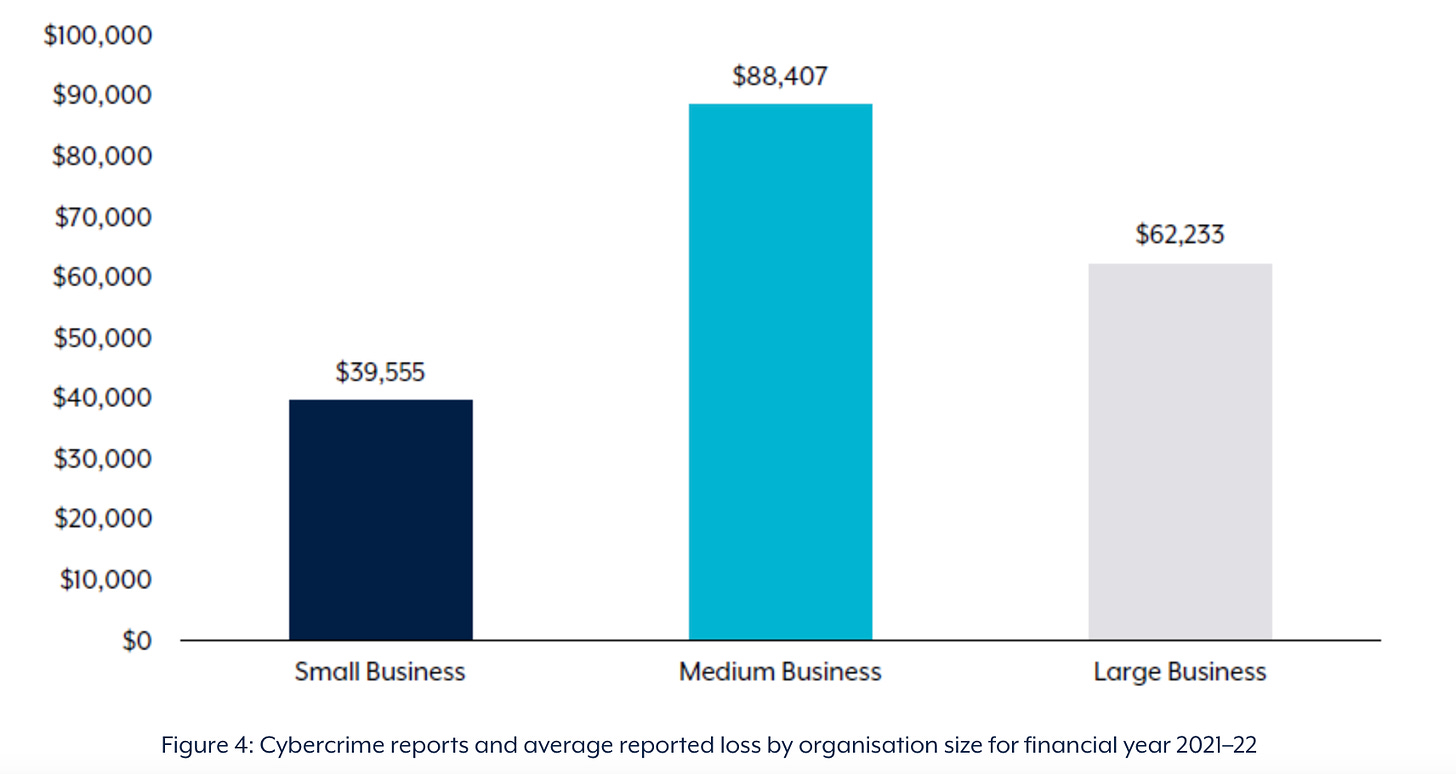
Chart of the week 📈
Let me get your juices going by showing you this week's chart of the week’.
Did you know that Medium-sized businesses (between 20 and 199 employees) had the highest average loss of $88,407 per cybercrime report last financial year? 😳
Do you run a small or medium-sized business? Do you have your cyber security affairs in order? If not, this is something you will want to start thinking about ASAP.
My Weekly Thoughts 💭
Real estate is hot property for hackers 🔥
Have you ever rented a house or purchased a property from a real estate company? If not, you surely have been exposed to the pinnacle of TV advertising by LJ Hooker (make sure your sound is on!)…
Okay, now that I got that free advertising for LJ Hooker out of the way (LJ, if you wanna slip me something for this I wouldn’t turn you down) let’s get back to the main event.
Those who have had the pleasure of doing business with real estate agents/ companies would know that they require a large amount of PI (Personal information - read more about it here) of yours. Especially when you are applying for rentals.
This ongoing collection of PI has always worried me and it should worry you too. The more PI you send out into the interwebs, the higher the risk of it being used against you if it ever falls into the wrong hands.
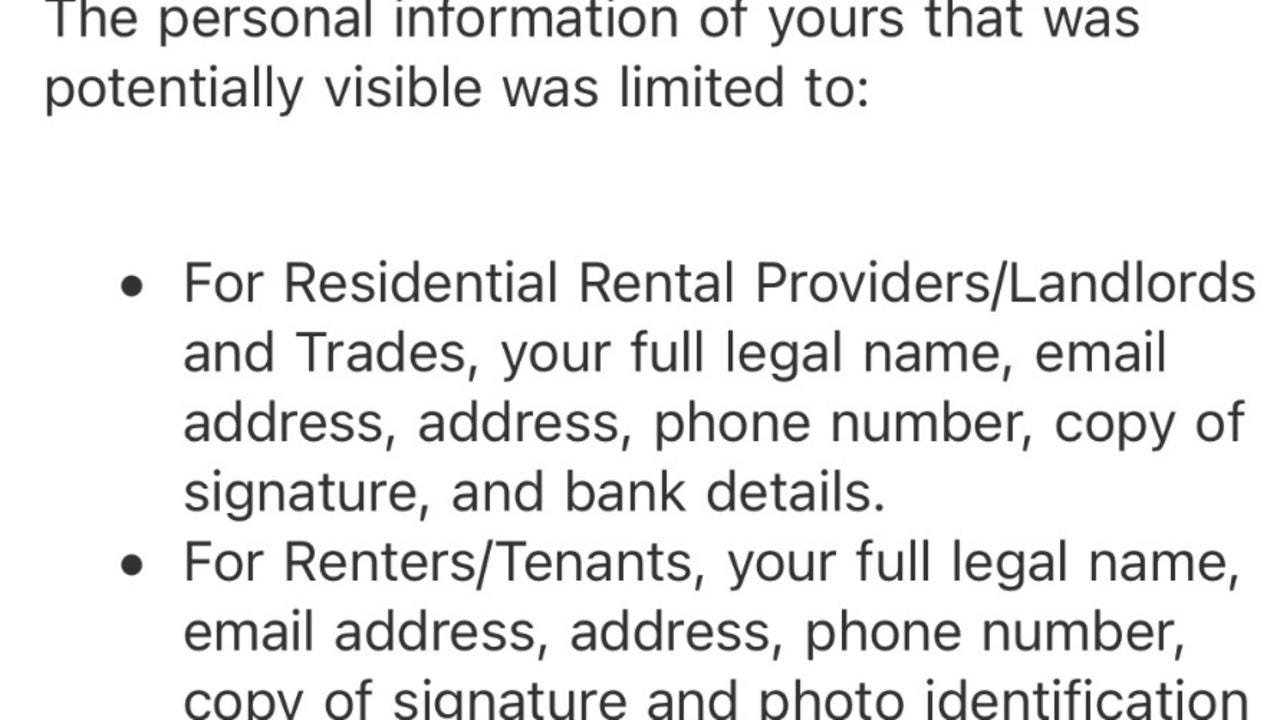
Last week it hit the news that real estate company Harcourts had suffered a data breach back in October, potentially exposing their customers’ names, addresses, signatures, photo ID and bank details.
Apparently, it was the compromise of an employee who worked for Stafflink, a company that offers a service to Harcourts and is used to manage its rental properties.
This individual was the way in for hackers/unwanted third parties to have a look around. Did they steal any of the data? Well, it hasn’t been confirmed but I have a feeling I know the answer.
Some of you may be wondering “How could this even happen?”. Well, a Harcourts spokesperson gave it to the media straight:
“We understand the unauthorised access occurred because the representative of Stafflink was using their own device for work purposes rather than a company-issued (and more secure) device.”
Not ideal but I think Harcourts cybers could have been better and the above just shouldn’t happen these days.
Harcourts have attempted to help its customers by offering complimentary credit monitoring services and access to the IDCARE support service; which I assume is quite busy at the moment.
As a renter myself I have had to provide a long list of PI to several real estate companies. This included sending through scanned copies of my drivers license or in some cases my passport.
As you could imagine I was extremely hesitant in doing so, offering up alternatives such as attending the office and showing them my ID but none wanted a bar of it and were stern on the point that they “needed copies”.
I requested a secure site where I could upload my documents. Not one of the 4 companies I dealt with had one.
So I took things into my own hands and decided to watermark copies of my ID which clearly outlined the company to which they were being sent, you know, so I could identify who had the breach if my docs were leaked.
From there I encrypted the documents in a password-protected zip file before sending them over super secure email (this is a joke BTW as email is not super secure) and sat back thinking I was super on the ball and I could at least get the files to them securely.
Except when I got the reply “Sorry, it looks like your files are corrupted can you please send them one by one?”
Me: “Gurrrrrl…. they are not corrupted and No I won’t”.
Long story short - I was a difficult customer and only shared my PI once I was locked in to secure a rental and even then I made sure I did so in person at their office. Even after it was all sorted I requested that any data not required to be saved on their end be deleted.
Since then, I have come to find out a few other ways to combat the above and will go into detail on these in the Cyber Advice section below.
Question for you: Have you shared data with a third party like the example above and taken action to have them purge the data? if so, leave me a comment.
Families & student data exposed 👩🎓
Another week, another government system breached.
This time a trusted government third party is the victim of a cyberattack and hackers are believed to have stolen data used by the Victorian Department of Education and Training. You can read about this one in more detail here.
The extent of the breach is still being investigated but I wanted to draw your attention to something that really worries me.
Apparently, data from the ‘Victorian school entrance health questionnaire’ was included in the information stolen.
This questionnaire is filled out by every family who has a student starting at a Victorian primary school, including public, private and independent schools.
This questionnaire doesn’t just have your run-of-the-mill PI in it! It includes sensitive personal information, including demographics, developmental and behaviours issues and even family alcohol or drug problems.
So, in this day and age, we (you, me, anyone you know) are not only having to worry about our own PI, but we also have to worry about the PI of our loved ones.
Now, for me, that means my kids who are only 4 and 2. But, if they were old enough to start school and we lived in Victoria, I could bet money that sensitive data about them and my meme addiction would now be in the hands of god knows who.
On that note, consider being extra vigilant about what info and data you hand over when it comes to your family and/or kids. Because at this rate, by the time my kids are adults, I wouldn’t be surprised if a large amount of their PI data (which they didn’t have a say in sharing in the first place) isn’t already out there somewhere.
Sweet Cyber Security Advice ✅
First of all, the unsolicited advice you are about to receive is targeted towards the everyday person.
If you are a business then the advice would also differ. If this is what you are after, I encourage getting in touch directly.
Furthermore, to keep this newsletter brief, I will link to guides already on the internet that cover the things mentioned.
So with that said, Let’s talk file sharing... The kind you want to practice when someone or a business wants you to hand over some cold hard information that could be used to identify you…or worse, impersonate you.
This is a huge topic that I’m only going to be able to scratch the surface of so let me focus on a few easy wins which relate to sharing data over email, which is more than likely the means by which you will be asked to do so anyway.
There are three easy ways to ensure you’re sending docs securely over email:
Encrypt the attachment
Password-protect the document
Share a link to the document
Encrypt the attachment
For the average person, the simplest way to encrypt the attachment/s you want to share is to do so by “zipping the files up”. Or in other words, taking the file/s you have and compressing them into 1 file, called a .zip file. A .zip file’s primary use is to compress multiple files into one giant file resulting in easy storage or sharing.
The cool thing you can do with a .zip file is you can password-protect the file.
Check out this guide on how to do this prior to sending a document and don’t forget you will need to share the password with whoever you want to have access via another means… like a phone call or message 😉.
Password-protect the document
If you are sharing a Microsoft Office document (such as a word or excel document) you could and should use the native password protection capabilities.
It’s an easy-to-implement, fast and consistent way to share office documents more securely. An approach that I would suggest applying to a business setting.
Check out Microsoft’s write-up here on how to protect a document with a password using the built-in features.
Share a link to the document
This is usually the approach I take when sharing data with others. And, yes I know that links and cybersecurity dont go well together but for the everyday person, the following will be better than just sending the data without any protections.
⚠️ Never click on any unsolicited links and if you are receiving this newsletter to your business email, always follow your companies endorsed file sharing policies/processes ⚠️
Essentially, I upload the file/s to a cloud platform (like dropbox or onedrive) and then take advantage of the inbuilt sharing capabilities by providing a link to the documents.
This approach can be used if you wanted to share files via email, whatsapp, signal or anywhere else you can share a link.
Depending on the service you use, there are a few options you will be able to tweak such as:
Password protecting access to the file/s - ie. A password is required to see the files
Enforcing expiry of sharing links - ie. The link will only work for a few days (or whatever you set)
Sharing with specific people - ie. Forcing someone to log in and prove who they are before accessing the file
For Microsoft onedrive, you could check out this guide. If you are looking to use another service and need a hand, leave me a comment and ill get back to you.
Thank you for hanging around to the end and reading what I have to write. This weeks edition was a little longer than I would like and will do my best to summarise future editions.
If you liked it please let me know by pressing the heart symbol or leaving me a comment. If you have any feedback or want me to write about something in particular, please let me know.
Have a great week!
Kyfer 🤙











@Kyfer, I am a bit reluctant to encourage the behaviour of sharing links ( Option 3 in your suggested file sharing). I have had my fair share of hair tearing experience as a blue teamer trying to educate users not to click on links or enter their passwords. Maybe there is a compensating control that we need to consider if we are suggesting option 3 as a secure file sharing mechanism.